TL; DR – AWS related modules dominate downloads from Terraform Registry, with a particular focus on Terraform modules for automating security groups.
We have been observing the growth in usage of Terraform from HashiCorp over the last few years. As we have noted previously interest in all of HashiCorps projects has shown substantial growth and Terraform is no exception here.
HashiCorp announced the Terraform Module Registry at their summit in September 2017. At the time we commented that this would become an interesting, and useful, resource for people. Enough time has passed to take an initial look at how the public repository is being used (HashiCorp also offer a private enterprise Terraform Module registry).
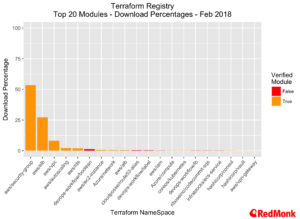
Modules are categorised across several dimensions, the most useful of these being “providers” – where a provider is a cloud provider. There are currently 376 modules in the repository, of which 42 are verified modules – modules which are reviewed by HashiCorp and are under active maintenance. Verified modules account for over 95% of all downloads. Total downloads at the time of writing are 965K, and we expect this to pass the one-million-mark next month.
AWS and the Terraform Registry
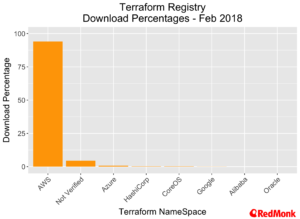
The usage of the public Terraform Registry is overwhelmingly biased towards Amazon Web Services, with over 94% of all module downloads related to one of the verified AWS modules. When we include unverified modules that are targeted to the AWS provider, this rises to over 97%.
Across the AWS related modules, the provider for security groups dominates, followed by the providers for Elastic Load Balancers and VPC. This is not surprising, it is rare to encounter AWS customers who find the configuration of security groups easy.
Kubernetes
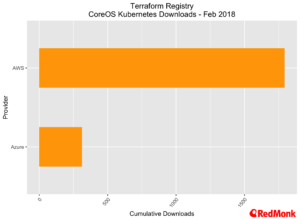
In our own conversations we hear Terraform mentioned in conjunction with Kubernetes reasonably regularly. While these numbers are far too small to draw any conclusions from, it was interesting to see the breakout of Kubernetes related downloads (less than 1% of the overall total) in relation to provider.
AWS dominates, but where Terraform has been used for installing CoreOS tectonic we see Azure coming in second. However, given Red Hats recent announcement of their intention to acquire CoreOS this usage of Terraform may change.
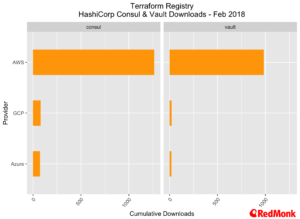
Consul and Vault
As we have noted previously both Consul and Vault are extremely popular components with users focused on developing cloud native applications. Here, we also see AWS taking the lion’s share of the downloads. As with the CoreOS commentary above the overall percentage of downloads is less than 1%.
Notes on this analysis: Data was gathered from the Terraform registry on February 19th, 2018. Downloads refer to cumulative downloads across versions.
Disclaimers: Amazon, Google, Microsoft, Oracle, CoreOS and Red Hat are all current RedMonk customers.
Lee Calcote says:
March 10, 2018 at 5:12 am
With the popularity of the CoreOS Tectonic Installer and AWS being the largest target for Kubernetes on Cloud, the Terraform Module Registry numbers here are understandable.