Over the last week we have had the opportunity to work with an interesting set of data collected by Anchore (full disclosure: Anchore is a RedMonk client). Anchore collected this data by means of a user survey ran in conjunction with DevOps.com. While the number of respondents is relatively small, at 338, there are some interesting questions asked, and a number of data points which support wider trends we are seeing around container usage. With any data set of this nature, it is important to state that survey results strictly reflect the members of the DevOps.com community.
The data set covered a number areas including container usage and plans, orchestration tools, operating system choices, CI tools and security. For this post we will be focusing on the data around containers and CI.
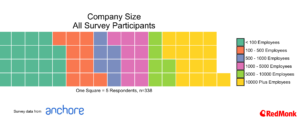
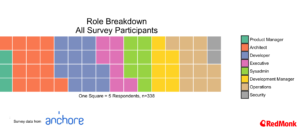
The Population
Our population breaks out with over 60% working in companies of greater than 100 people, and with an interesting distribution across a variety of roles.
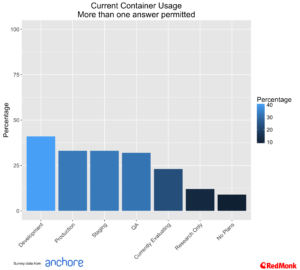
Container Usage Breakdown
Matching other trends that we are tracking approximately one third of the participants are running containers in production, with development coming in slightly higher.
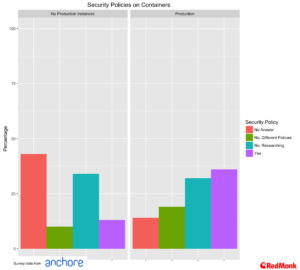
Security as a Question
One of the most interesting aspects of this survey data was the focus on security. In particular we found it interesting to see what type of security policies that enterprises running in production had versus those that did not.
It is particularly interesting to see that companies were far more likely to be running in production where they had a defined policy in place. There a lot of underlying aspects to drill into here, but at its highest level developer enthusiasm for a technology rarely runs as far as security, and almost never considers some of the more detailed compliance nuances that an enterprise must consider.
Bluntly put this presents a barrier to adoption, and an opportunity for conservative organisations to hold off on adopting new technologies.
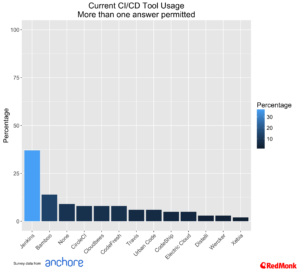
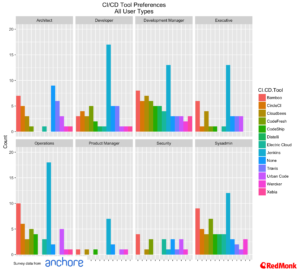
CI/CD and The Enterprise On Ramp
Here at RedMonk we have been talking about the importance of CI/CD as the on-ramp for all things cloud native, and have seen Jenkins taking a strong lead over other tools. This trend is once again repeated in the Anchore data, with the combination of Jenkins and CloudBees (commercial Jenkins) approaching 50%.
As we would expect with the audience for this survey, the level of usage of CI/CD is a good deal higher than we have seen in other areas.
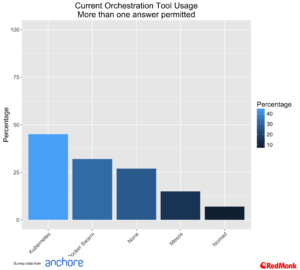
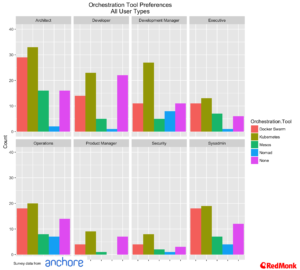
Orchestration Tools
To say that the orchestration tools space is hot would be somewhat of an understatement. For the purposes of this analysis we have combined Red Hat’s OpenShift and CoreOS Tectonic under the Kubernetes banner, and Apache Mesos and Mesosphere under the Mesos banner.
We can see that Kubernetes and Docker Swarm have by far the most take up, with Kubernetes in a slight lead across all user types
Interestingly Mesos still features strongly with architects. Among developer communities we very rarely hear Mesos mentioned anymore. On the other hand we frequently encounter architects have invested in Mesos from the perspective of their big data environments and are looking at a common approach for their container strategy. That said, this entire market is extremely fluid at the moment.
A Look at the Operating Systems of Containers
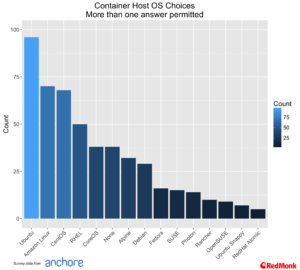
Host Operating Systems
Rather unsurprisingly Ubuntu takes the lead in container host operating systems, but two other aspects of this data are also worthy of further comment. Firstly, the high usage of Amazon Linux is a reflection on the growth in usage of ECS, while the use of Alpine Linux being used as a host operating system reflects usage of Docker for Mac.
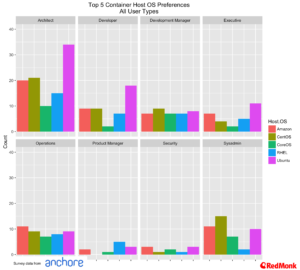
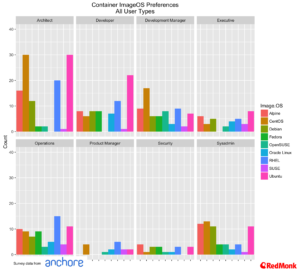
Looking at the top five host operating systems across user roles we see Ubuntu having a particular strong lead among developers and architects.
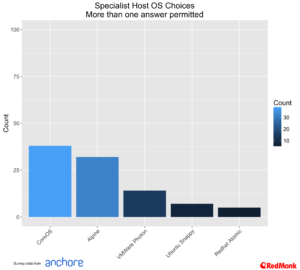
The usage of specialist operating systems is something that we see growing, but currently hitting a chasm point, something which Garret Rushgrove noted in a recent post. Among specialist operating systems CoreOS has a lead, and Alpine continues to grow, although as noted above part of this growth reflects the usage of Docker on Mac.
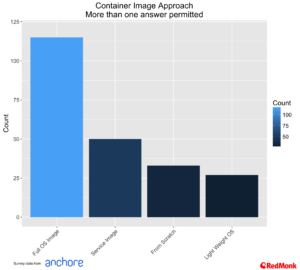
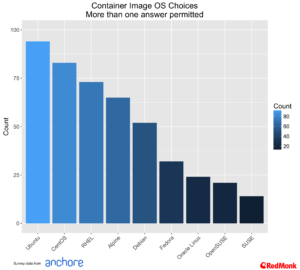
Container Image Operating Systems
Part of the promise of containers is simplified application stacks, with the ability to bundle everything required for an application, or components of application in a single package. Too often, however, people confuse this with an easy alternative to VMs. This is evident in this data as well, as we can see by the number of respondents who base their container images on full OS images.
Looking at the choice of images, Ubuntu once again leads, with CentOS and RHEL as the next most popular.
All of this raises some wider questions in terms of education. For most applications you do not need a full OS image. However, the reality is such that, in at least the medium term, many applications will be built on top of such images for a variety of reasons – be they simplicity and developer choice, or for operational reasons such as existing compliance procedures, security policies and so forth.
That said, the idea of building containers from full OS images raises multiple questions from maintenance, security and deployment perspectives. The velocity of change for microservice based applications in containers raise a number of interesting challenges – from a developer perspective it is very easy to spin up and release a new version of a service. Indeed, slowing this process down in anyway is the very antithesis of everything a cloud native approach promises.
This leads us to a very difficult operational problem – how do we ensure security, and understand the makeup of an application while still allowing developer velocity to increase. On the security front in particular we see developers reassuring themselves that being aware of CVE scores is more than enough security – this is no doubt a useful baseline, but it is far from enough.
Disclaimers: Anchore, Atlassian, IBM, Docker, RedHat, Amazon and CoreOS are current RedMonk clients.
Containers in Production – Is Security a Barrier? A Dataset from Anchore - Anchore says:
December 1, 2016 at 11:31 pm
[…] Read Article Search for: […]
KubeWeekly #62 – KubeWeekly says:
December 5, 2016 at 3:35 pm
[…] Containers in Production – Is Security a Barrier? A Dataset from Anchore […]
KubeWeekly #63 – KubeWeekly says:
December 5, 2016 at 3:36 pm
[…] Containers in Production – Is Security a Barrier? A Dataset from Anchore […]
Links 13/12/2016: CoreOS Container Linux, CentOS Linux 7 | Techrights says:
December 13, 2016 at 11:06 am
[…] Containers in Production – Is Security a Barrier? A Dataset from Anchore […]
Containers are Linux – OpenShift Blog says:
April 13, 2017 at 4:30 pm
[…] from do-it-yourself container solutions to supported container platforms. Security concerns are often cited as one of the main barriers to container adoption in production. This is the case with any new […]
The breadth and reach of the OpenShift marketplace – OpenShift Blog says:
May 13, 2017 at 9:40 pm
[…] on recent survey data (by RedMonk, Rightscale, PortWorx, Sysdig, Anchore), from both independent analysts and usage-based metrics, […]